


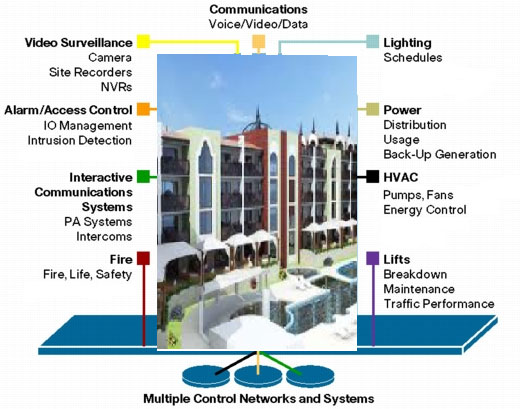
We offer a single platform solution that encompasses many functions of present systems, namely -
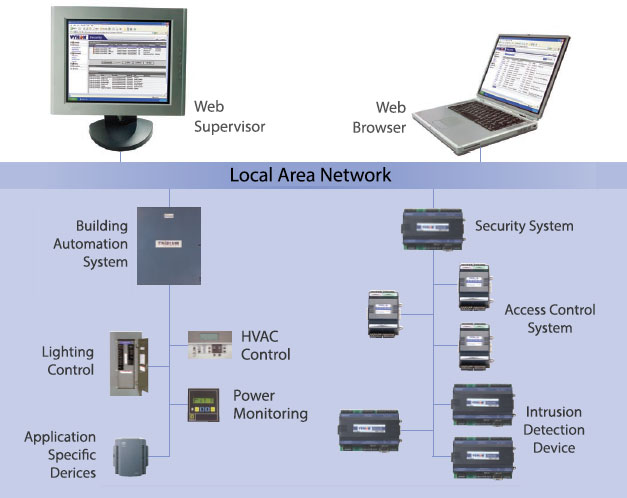
Now, customers can source a comprehensive solution from a single vendor and enjoy the benefits of IP-enabled systems, such as distributed monitoring from central location with messaging and alerting options, not technologically feasible before!


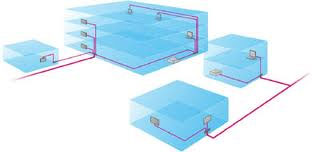
Connectivity options for Inter building campus wide connectivity include fiber optic or wireless networking.

In this scenario, there is the Fiber optic option or in-building wireless system for comprehensive building wide coverage.

The proposed system addresses the issue of lack of integrity as found in most systems. The deploying authorities require systems that are able to operate easily and reliably under a variety of operational and environmental conditions and that are not prone to false alarms and nuisance alarms. With confidence in the integrity of the monitoring system being a major concern today, new technology employing advanced distributed fiber optic sensors provide a reliable and cost-effective intrusion detection technology. These technology solutions come in two flavours, namely, “in-fence” deployment and “in ground” deployment for intrusion detection.
The multi-zone fiber optic sensor cable can be mounted to rigid fencing and/or buried in trenches around a perimeter for optimum monitoring of acoustic disruptions. The system uses high-fidelity reproduction and classification to accurately alarm upon detection of any noise or vibration that indicates tampering, intrusion, digging, operating of machinery or vehicles, and any other breaching events near the cable’s location.


“In fence” intrusion detection is a monitoring system that detects the first signs of intrusion at the fence line, performing easily and reliably under a wide variety of operational and environmental conditions with an extremely low false alarm and nuisance alarm rates.

This consists of a buried fiber optic perimeter security system designed to detect and verify personnel, animals, walking, running, digging, or the operation of machinery/vehicles near the sensing cable.

The buried fiber optic cable system replaces more expensive, unreliable, bulky electronic sensors currently used in existing conventional perimeter security systems with a low cost, ultra-reliable fiber optic sensor cable.
Smart Monitoring Technologies defines the concept of Smart Factories, Mines, Processing Plants, Agriculture, Wide area energy / process monitoring. Behind this concept lies a mix of technologies serving the factory of the future.
Connect the machines to the Internet, through the Internet of Things, collect the data in your own secure server directly, bypassing the typical LoRA cloud (shared & hosted data servers), treat them through Artificial Intelligence algorithms, so as to optimize the Operations, reduce costs through preventive / predictive maintenance. In a general way, to allow an optimized and centralized management of its installations, its equipment, its machines. Offer better operational and business tools.

Whatever the type of machine, it is always possible to recover the data in order to analyze them. Any type of protocol: FTP, MTQQ, M-BUS, ModBus, RS232, RS485. Any type of network: WIFI, M2M, LoRa, ZigBee ...

Process data and provide reports and dashboards for the various stakeholders: Support, Management, Customers.

Data analysis must anticipate failures or non-optimized processes. To be able to intervene quickly in the event of a problem, or even to prevent future problems.

The Small Vertical Axis Wind Turbine (SVAWT)’ design & cost factors make them a viable source of renewable energy in residential/ cosmopolitan areas.


ID Badges and Access Control - Most organizations today require a performing and efficient access control system. There are many reasons for having such a system and these include:
RFID technology is quickly becoming a popular choice since the advancement in technology makes a variety of solutions available to any organization. There are major deficiencies in the legacy solutions that use the traditional access control systems. Barcodes, magnetic stripes, and proximity readers all rely on the user to either make contact or place the badge very close to the reader. In addition, bar codes can only be read one at a time and the respective embedded information cannot be updated. Such limitations can be cumbersome and time consuming.
An RFID access control system can provide an easy and efficient solution. RFID badges can be read from much further distances than other traditional technologies and the embedded electronic information for each badge can be over-written repeatedly. The increased reading distance thus enables other tracking technologies like surveillance cameras to be activated in conjunction with an employee being in their vicinity. Furthermore, multiple RFID badges can be read all at the same time. Information about employee access, attendance, and duties performed, can be easily and efficiently monitored and stored in a database. Access information can also be tied to a Windows Active Directory or LDAP for user authentication and therefore be synchronized to an authorized access scheme.



Home Automation System - including cooling control, ventilation control, lighting controls, curtain controls, irrigation control and other electrical controls, consumption measurements, access control, intruder alarms, smoke/heat alarms, leakage/moisture alarms, gas alarms, cameras and video monitoring, IP intercom and audio distribution.
